Create IAM Role for DynamoDB Backup
Objective: Create the IAM role DynamoDBBackupRole for the Lambda function
BackupDynamoDBAndSendEmail, granting permissions to read and write data to the DynamoDB tablestudentData, store backup files in S3, send emails via SES, log data to CloudWatch, and support potential interactions with CloudFront.
The function BackupDynamoDBAndSendEmail performs:
- Reads student data (Student ID, Full Name, Class, Date of Birth, Email) from the DynamoDB table
studentDatavia the Scan operation. - Stores a JSON file in an S3 bucket (e.g.,
student-backup-20250706). - Creates a pre-signed URL for the backup file and sends a notification email via SES (e.g., to
nguyentribaothang@gmail.com). - Logs data to CloudWatch for monitoring.
This role needs:
- Permissions to read and write data to DynamoDB (
AmazonDynamoDBFullAccess). - Permissions to store and create URLs on S3 (
AmazonS3FullAccess). - Permissions to send emails via SES (
AmazonSESFullAccess). - Permissions to log data to CloudWatch (
AWSLambdaBasicExecutionRole). - Permissions for CloudFront (
CloudFrontFullAccess) for potential future features.
Note:
CloudFrontFullAccessis not currently used but is retained for future functionalities (e.g., managing CloudFront distributions).
Detailed Steps
Below are the detailed steps to create the IAM role DynamoDBBackupRole:
1. Access the AWS Management Console
-
Open your browser and log in to the AWS Management Console with your AWS account.
-
In the search bar, type IAM and select Identity and Access Management (IAM).
-
Ensure you are in the correct AWS region (e.g.,
us-east-1), check in the top right corner.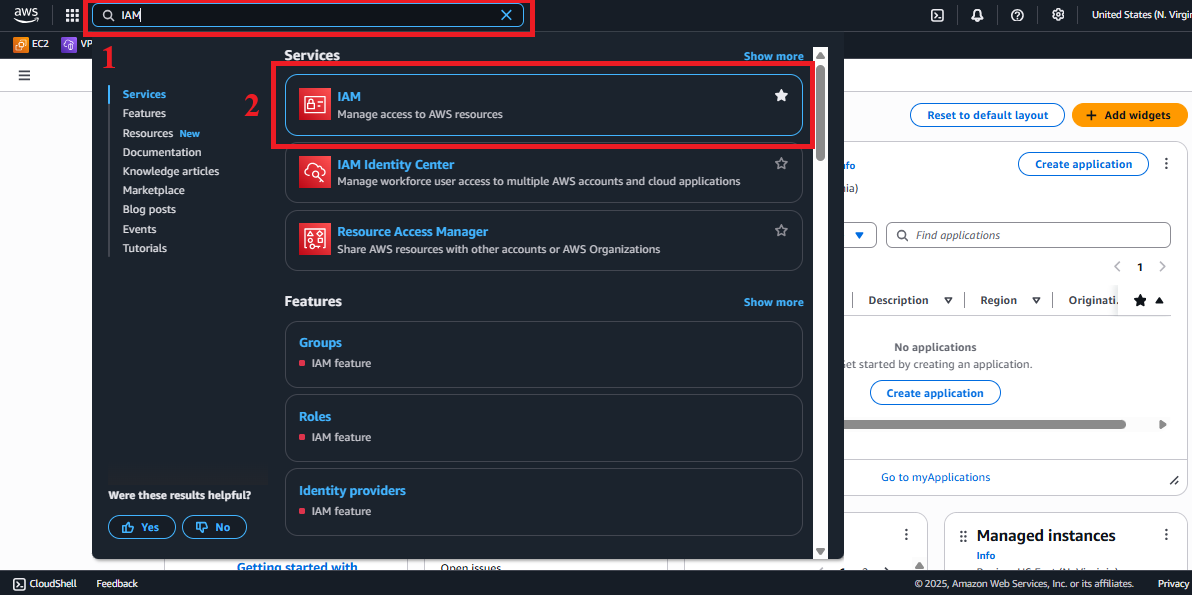 Figure 1: AWS Console interface with the IAM search bar.
Figure 1: AWS Console interface with the IAM search bar.
2. Navigate to the Roles Section
-
In the IAM interface, find the left-hand navigation menu.
-
Select Roles to view the list of IAM roles. If no roles exist, the list will be empty.
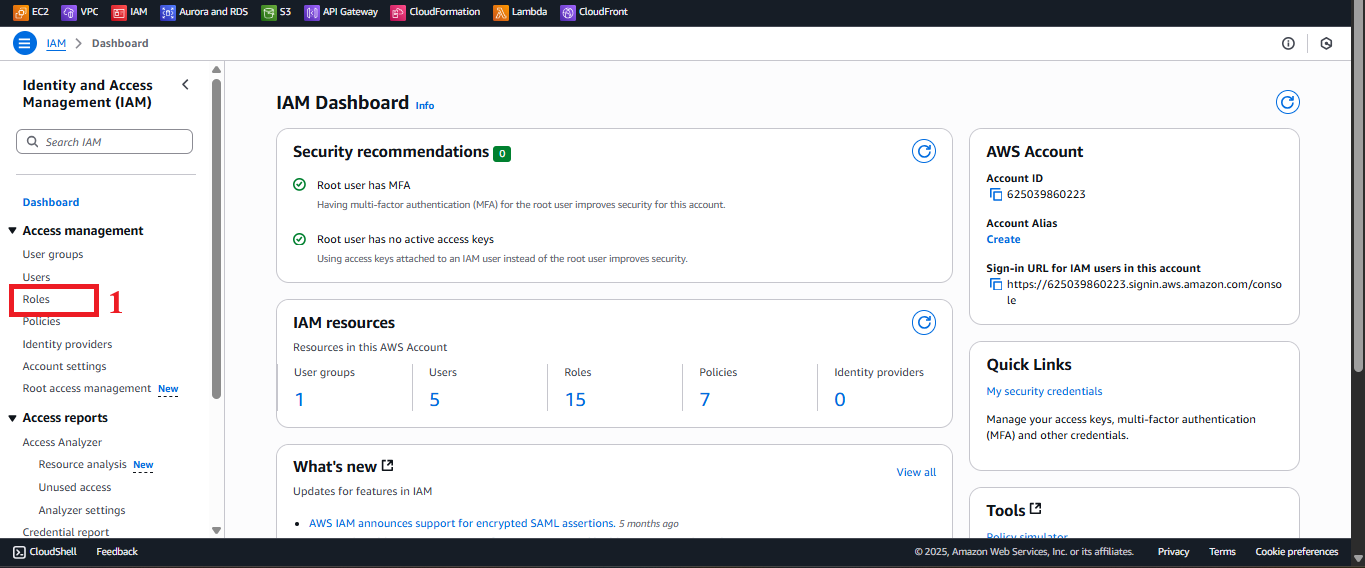 Figure 2: Navigation menu with the Roles option.
Figure 2: Navigation menu with the Roles option.
3. Start the Role Creation Process
-
In the Roles interface, click the Create Role button in the top-right corner.
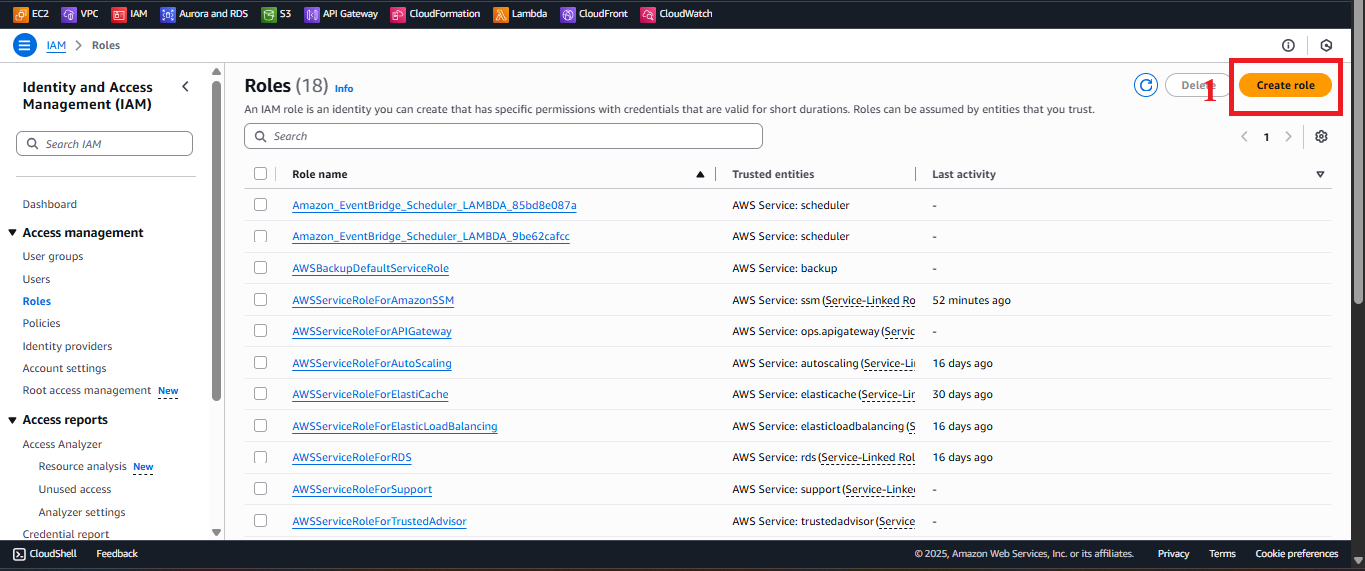 Figure 3: Create Role button in the Roles interface.
Figure 3: Create Role button in the Roles interface.
4. Choose Trusted Entity Type
-
In the Select trusted entity section, choose AWS Service to specify that the role is for an AWS service.
-
In the Use case section, select Lambda from the list of services.
-
Click Next to move to the permission configuration step.
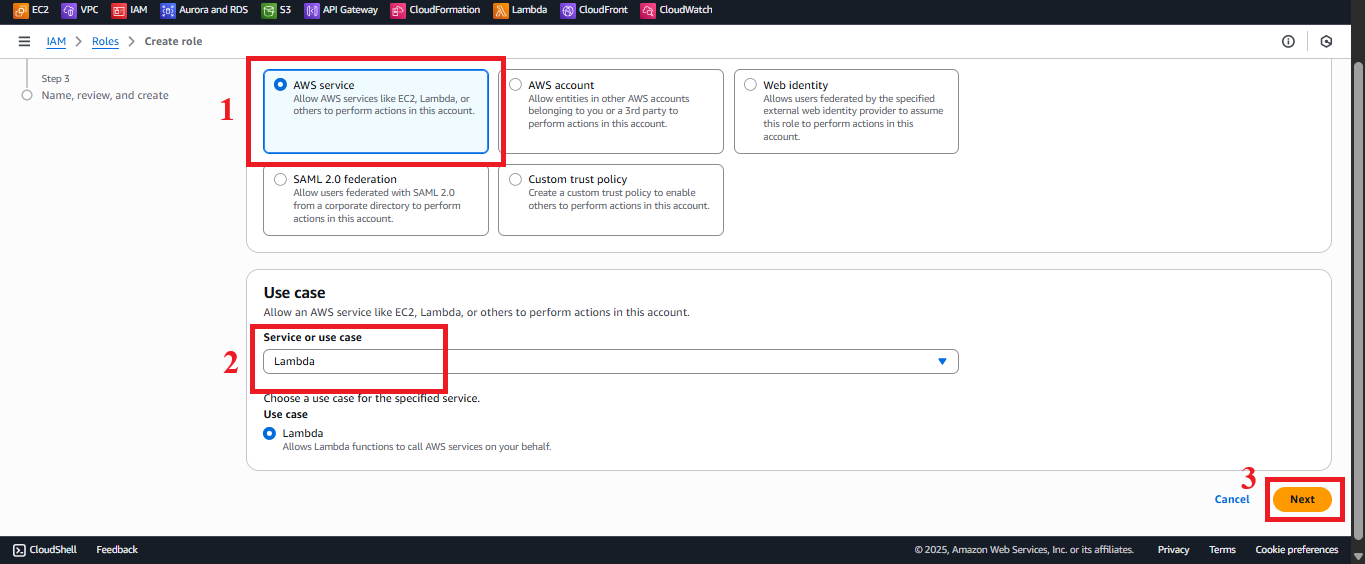 Figure 4: Choosing AWS Service and Lambda in Use case.
Figure 4: Choosing AWS Service and Lambda in Use case.
5. Grant Permissions to the Role
-
In the Permissions section, add the following five policies:
-
AmazonDynamoDBFullAccess:
- Type
AmazonDynamoDBFullAccessin the search bar. - Select the AmazonDynamoDBFullAccess policy.
Description: Grants read and write access to DynamoDB, supporting operations like Scan and other operations if needed.
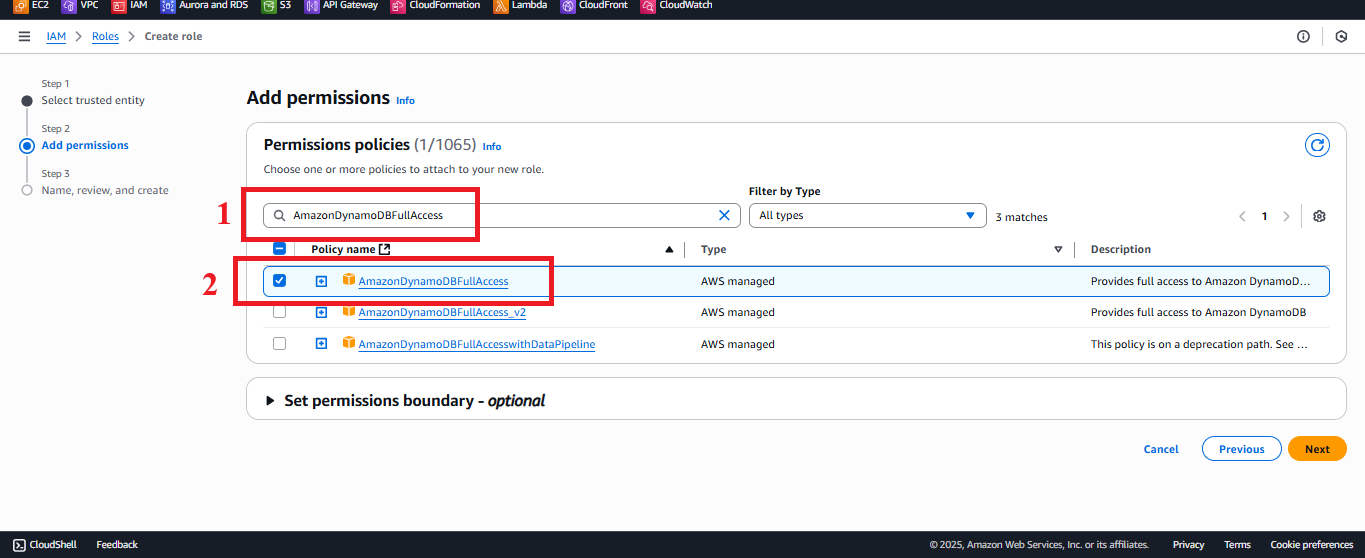 Figure 5: Selecting the AmazonDynamoDBFullAccess policy.
Figure 5: Selecting the AmazonDynamoDBFullAccess policy. - Type
-
AmazonS3FullAccess:
- Type
AmazonS3FullAccessin the search bar. - Select the AmazonS3FullAccess policy.
Description: Grants permissions to store backup files in S3 (
PutObject) and create pre-signed URLs (GeneratePresignedUrl).
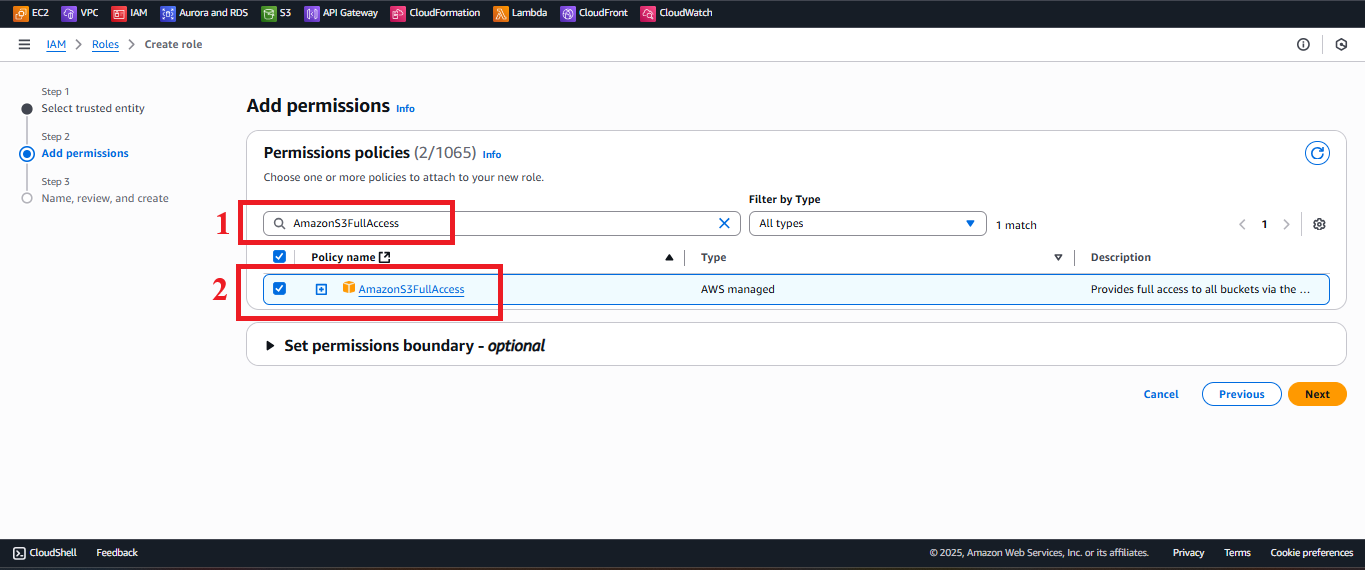 Figure 6: Selecting the AmazonS3FullAccess policy.
Figure 6: Selecting the AmazonS3FullAccess policy. - Type
-
AmazonSESFullAccess:
- Type
AmazonSESFullAccessin the search bar. - Select the AmazonSESFullAccess policy.
Description: Grants permission to send emails via SES to notify users with a backup download link (e.g., to
nguyentribaothang@gmail.com).
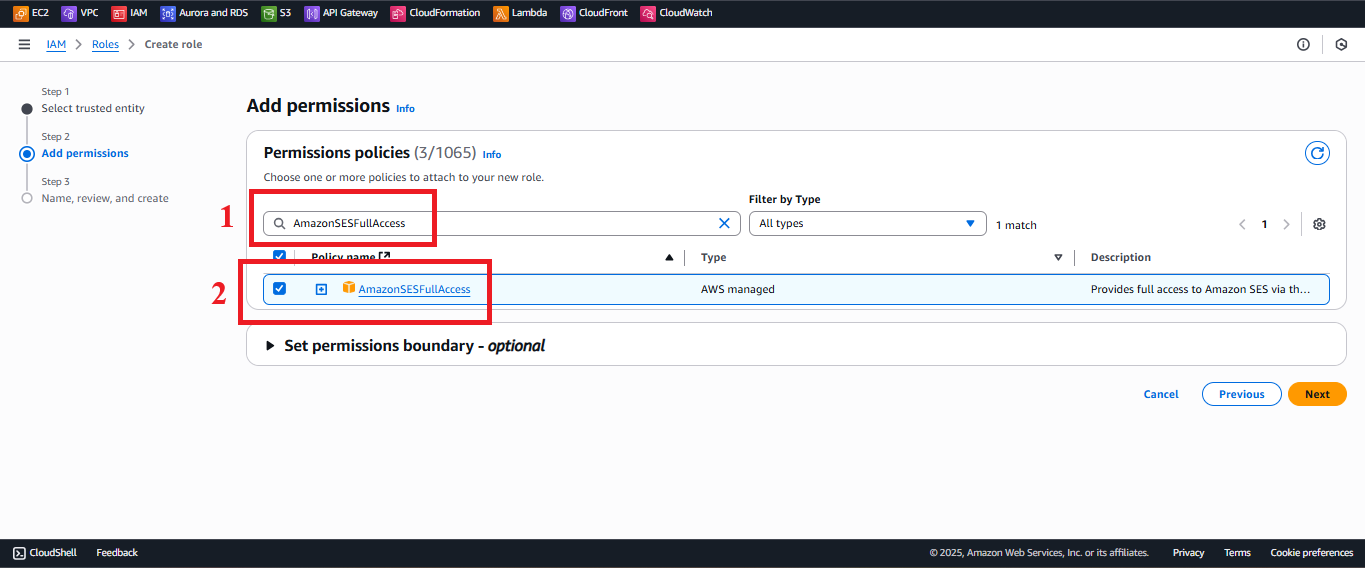 Figure 7: Selecting the AmazonSESFullAccess policy.
Figure 7: Selecting the AmazonSESFullAccess policy. - Type
-
AWSLambdaBasicExecutionRole:
- Type
AWSLambdaBasicExecutionRolein the search bar. - Select the AWSLambdaBasicExecutionRole policy.
Description: Allows the Lambda function to log to CloudWatch for monitoring and debugging.
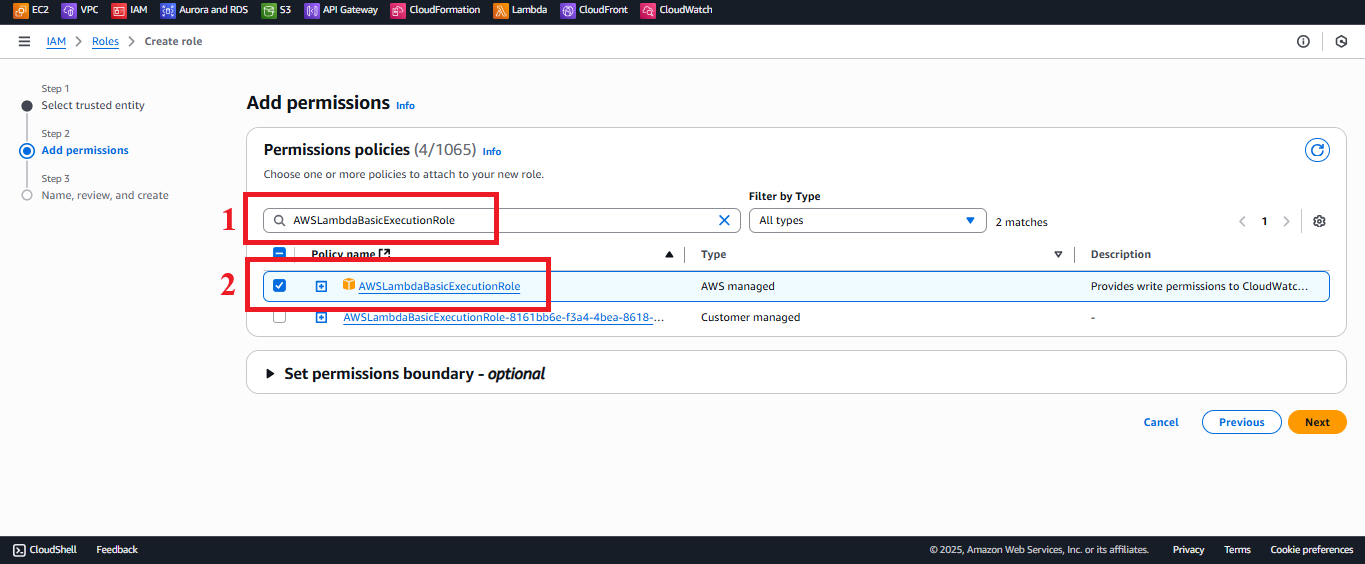 Figure 8: Selecting the AWSLambdaBasicExecutionRole policy.
Figure 8: Selecting the AWSLambdaBasicExecutionRole policy. - Type
-
CloudFrontFullAccess:
- Type
CloudFrontFullAccessin the search bar. - Select the CloudFrontFullAccess policy.
Description: Grants permission to manage CloudFront distributions for potential future features.
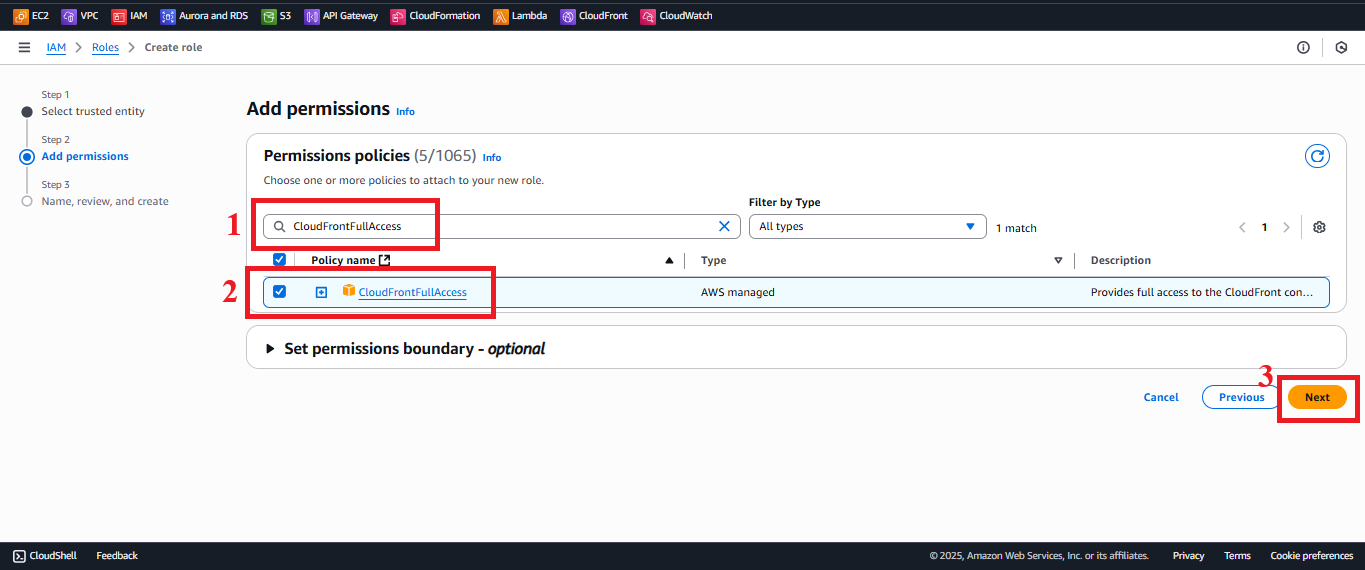 Figure 9: Selecting the CloudFrontFullAccess policy.
Figure 9: Selecting the CloudFrontFullAccess policy. - Type
-
-
Verify the list of Permissions policies to ensure it includes:
AmazonDynamoDBFullAccessAmazonS3FullAccessAmazonSESFullAccessAWSLambdaBasicExecutionRoleCloudFrontFullAccess
-
Click Next.
6. Name and Review the Role
-
In the Role details section:
- Role Name: Enter
DynamoDBBackupRole.Note: The name must match exactly with the Lambda function configuration for
BackupDynamoDBAndSendEmail. - Description (optional): Enter a description, e.g., “IAM role for Lambda function BackupDynamoDBAndSendEmail, granting read and write access to DynamoDB, store backups to S3, send emails via SES, log to CloudWatch, and support CloudFront.”
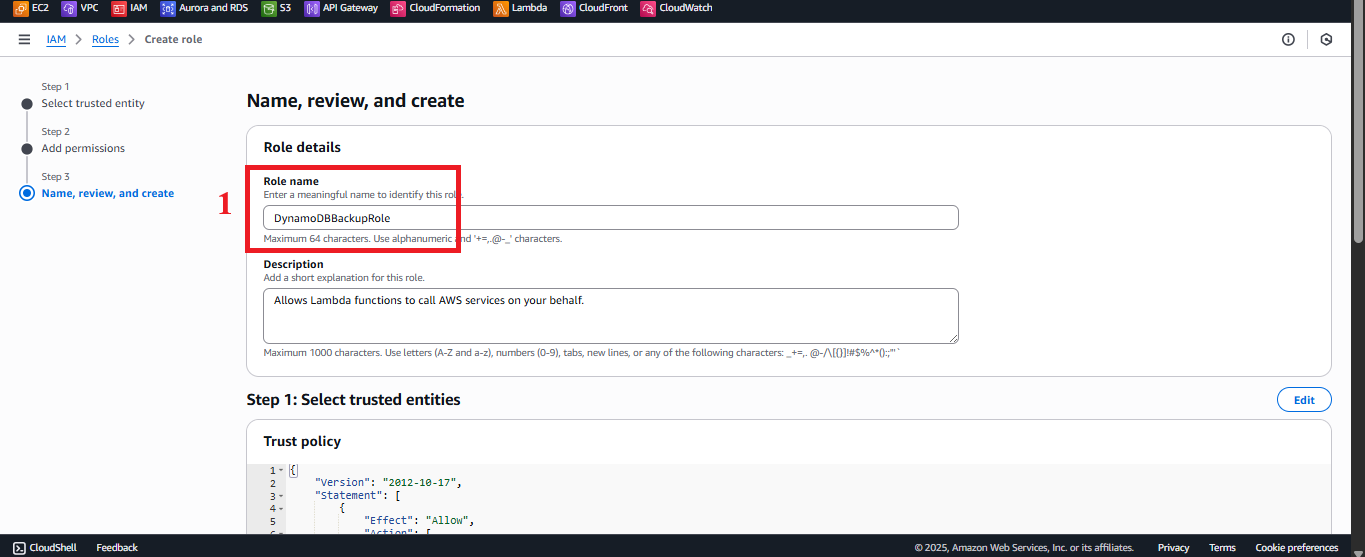 Figure 10: Enter role name and description.
Figure 10: Enter role name and description. - Role Name: Enter
-
Double-check:
- Trusted entity: AWS Service (Lambda).
- Permissions:
AmazonDynamoDBFullAccess,AmazonS3FullAccess,AmazonSESFullAccess,AWSLambdaBasicExecutionRole,CloudFrontFullAccess.
-
Click Create Role.
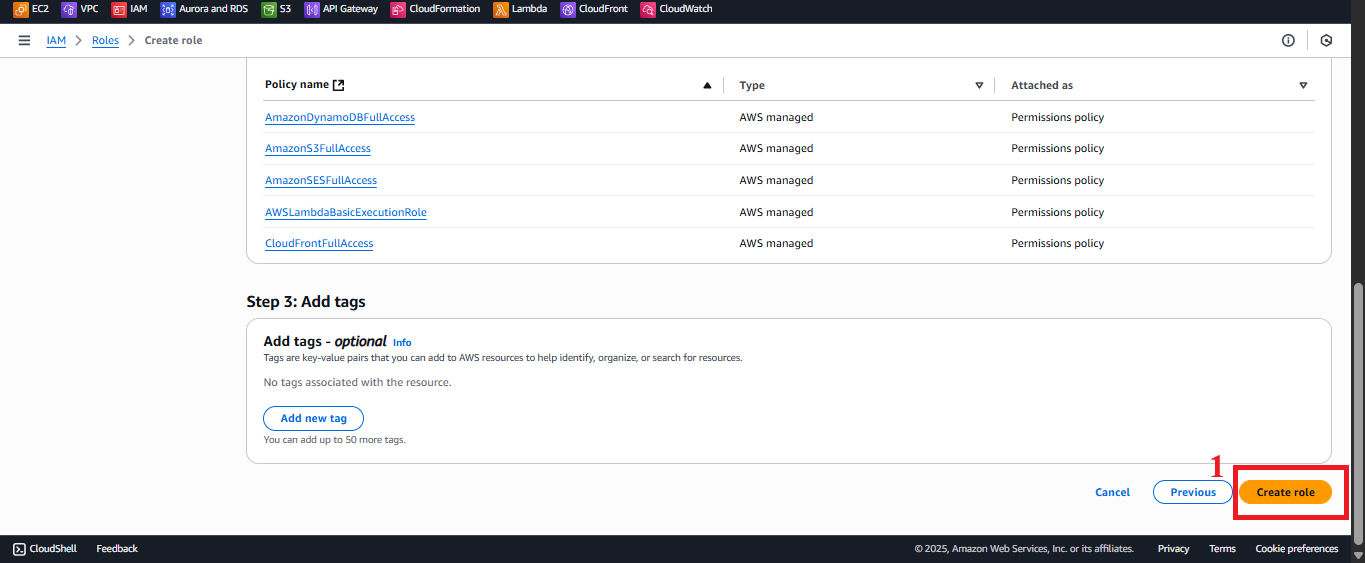 Figure 11: Create Role button to finalize the creation.
Figure 11: Create Role button to finalize the creation.