Create IAM Role for Lambda Get
Objective: Create the IAM role LambdaGetStudentRole for the Lambda function
getStudentData, granting permissions to read data from the DynamoDB tablestudentData, log data to CloudWatch, and support potential interactions with S3 and CloudFront.
The function getStudentData performs a Scan operation to retrieve all student data (Student ID, Full Name, Class, Date of Birth, Email) from the DynamoDB table studentData. This role needs to include:
- Permissions to log data to CloudWatch (
AWSLambdaBasicExecutionRole). - Permissions to read data from DynamoDB (
AmazonDynamoDBReadOnlyAccess). - Permissions for S3 and CloudFront (
AmazonS3FullAccess,CloudFrontFullAccess) for potential future features.
Note:
AmazonS3FullAccessandCloudFrontFullAccessare not currently used in the code, but are retained for future functionalities (e.g., saving files to S3 or managing CloudFront).
Detailed Steps
Below are the detailed steps to create the IAM role LambdaGetStudentRole:
1. Access the AWS Management Console
-
Open your browser and log in to the AWS Management Console with your AWS account.
-
In the search bar at the top of the page, type IAM and select Identity and Access Management (IAM).
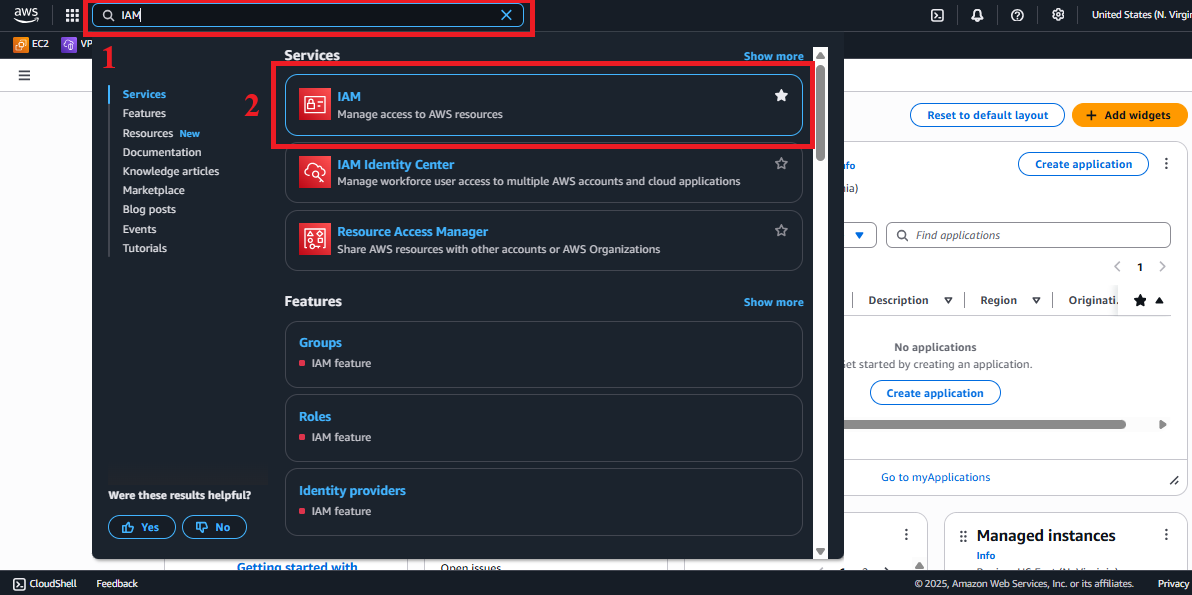 Figure 1: AWS Console interface with the IAM search bar.
Figure 1: AWS Console interface with the IAM search bar.
2. Navigate to the Roles Section
-
In the IAM interface, find the left-hand navigation menu.
-
Select Roles to view the list of IAM roles. If no roles exist, the list will be empty.
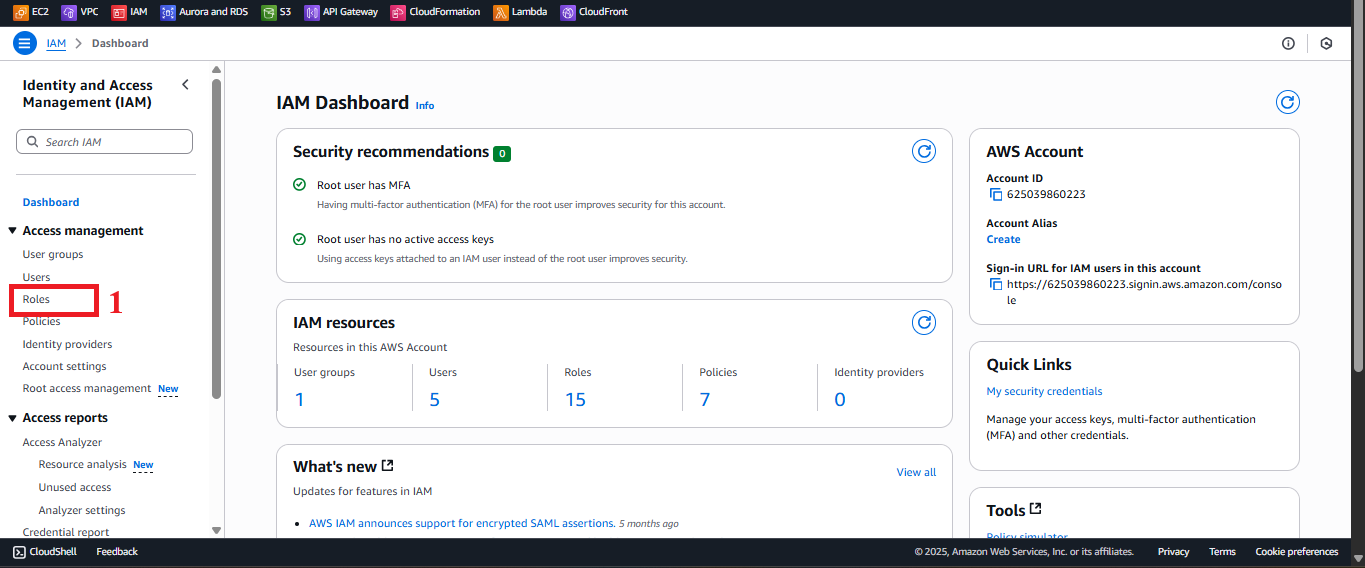 Figure 2: Navigation menu with the Roles option.
Figure 2: Navigation menu with the Roles option.
3. Start the Role Creation Process
-
In the Roles interface, click the Create Role button in the top-right corner.
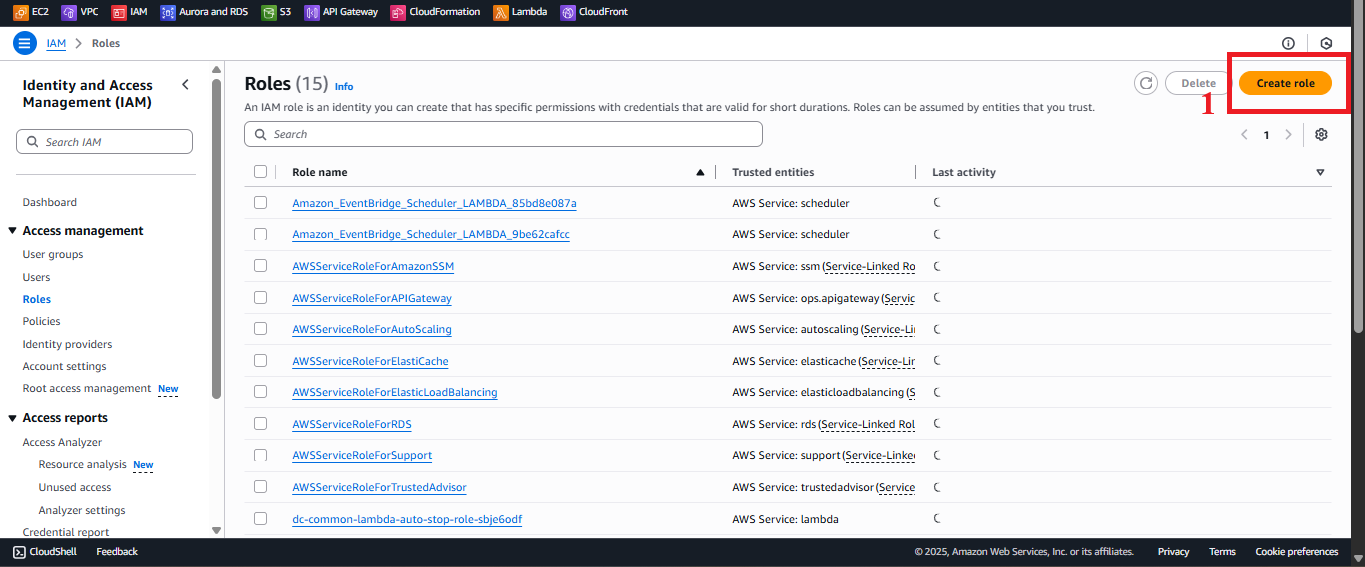 Figure 3: Create Role button in the Roles interface.
Figure 3: Create Role button in the Roles interface.
4. Choose Trusted Entity Type
-
In the Select trusted entity section, choose AWS Service to specify that the role is for an AWS service.
-
In the Use case section, select Lambda from the list of services.
-
Click Next to move to the permission configuration step.
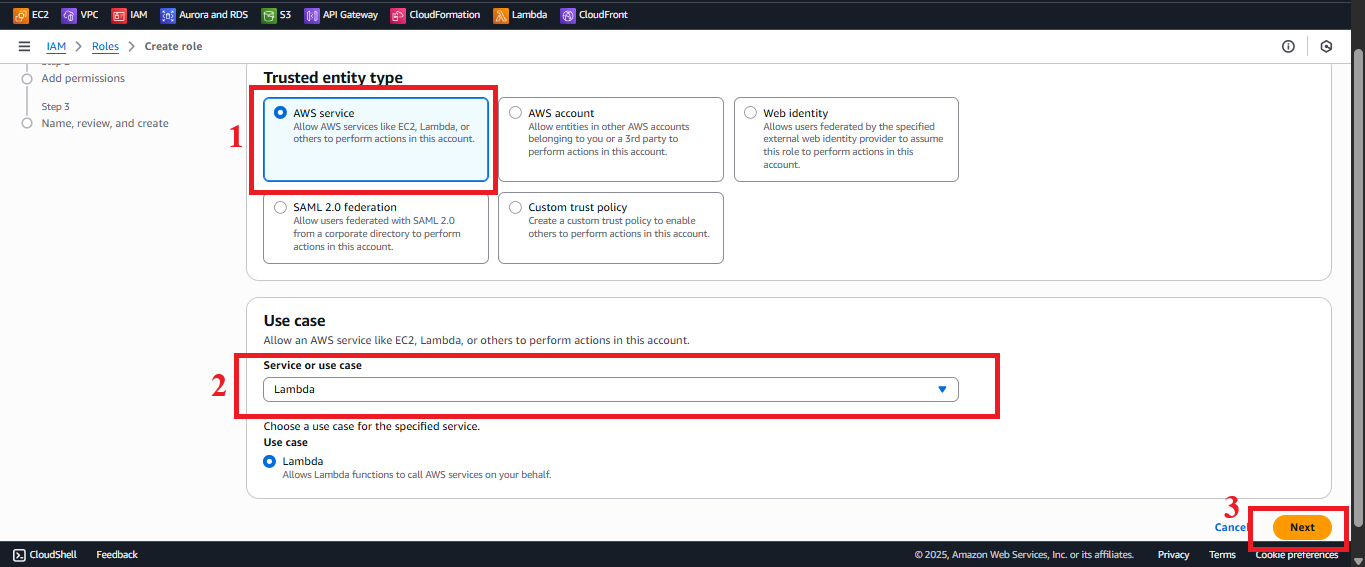 Figure 4: Choosing AWS Service and Lambda in Use case.
Figure 4: Choosing AWS Service and Lambda in Use case.
5. Grant Permissions to the Role
-
In the Permissions section, add the following four policies:
-
AWSLambdaBasicExecutionRole:
- Type
AWSLambdaBasicExecutionRolein the search bar. - Select the AWSLambdaBasicExecutionRole policy.
Description: Allows Lambda functions to log to CloudWatch for monitoring and debugging.
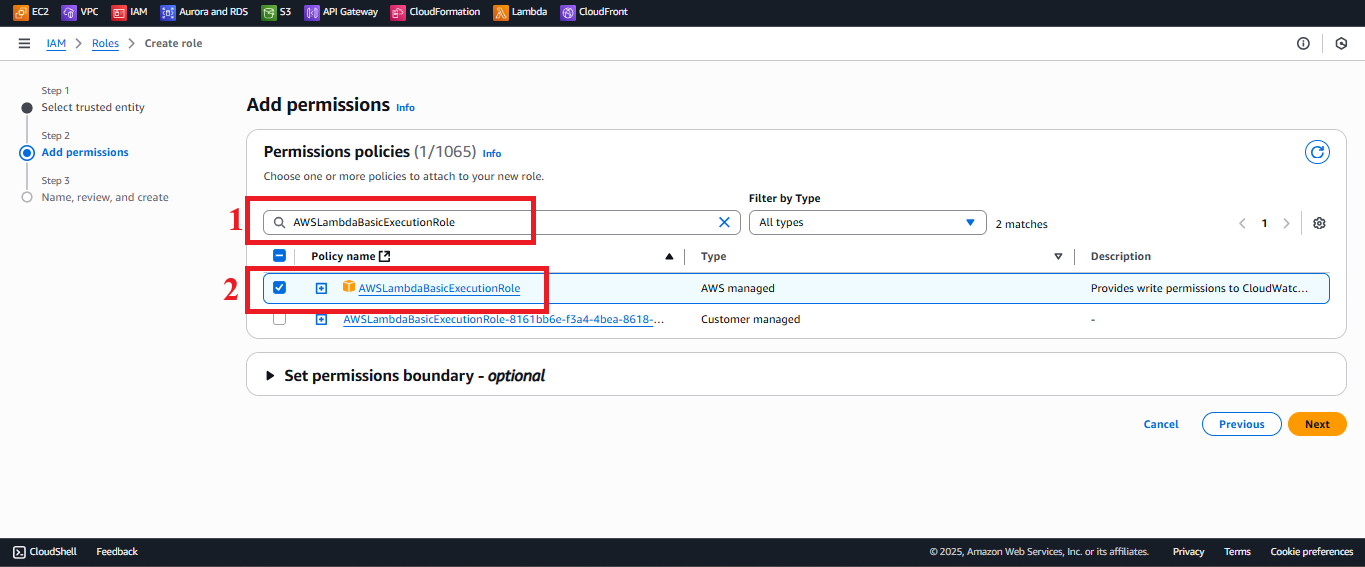 Figure 5: Selecting the AWSLambdaBasicExecutionRole policy.
Figure 5: Selecting the AWSLambdaBasicExecutionRole policy. - Type
-
AmazonDynamoDBReadOnlyAccess:
- Type
AmazonDynamoDBReadOnlyAccessin the search bar. - Select the AmazonDynamoDBReadOnlyAccess policy.
Description: Grants read-only access to DynamoDB, supporting operations like Scan or GetItem.
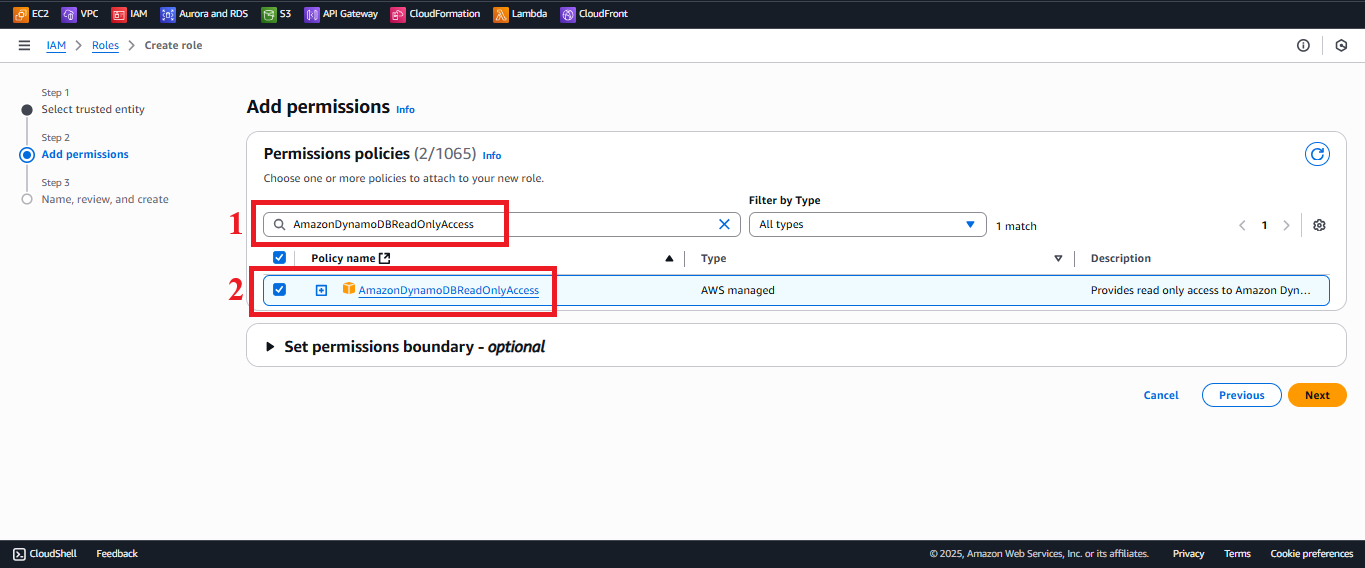 Figure 6: Selecting the AmazonDynamoDBReadOnlyAccess policy.
Figure 6: Selecting the AmazonDynamoDBReadOnlyAccess policy. - Type
-
AmazonS3FullAccess:
- Type
AmazonS3FullAccessin the search bar. - Select the AmazonS3FullAccess policy.
Description: Grants read, write, and manage S3 buckets for potential future features (e.g., storing additional files).
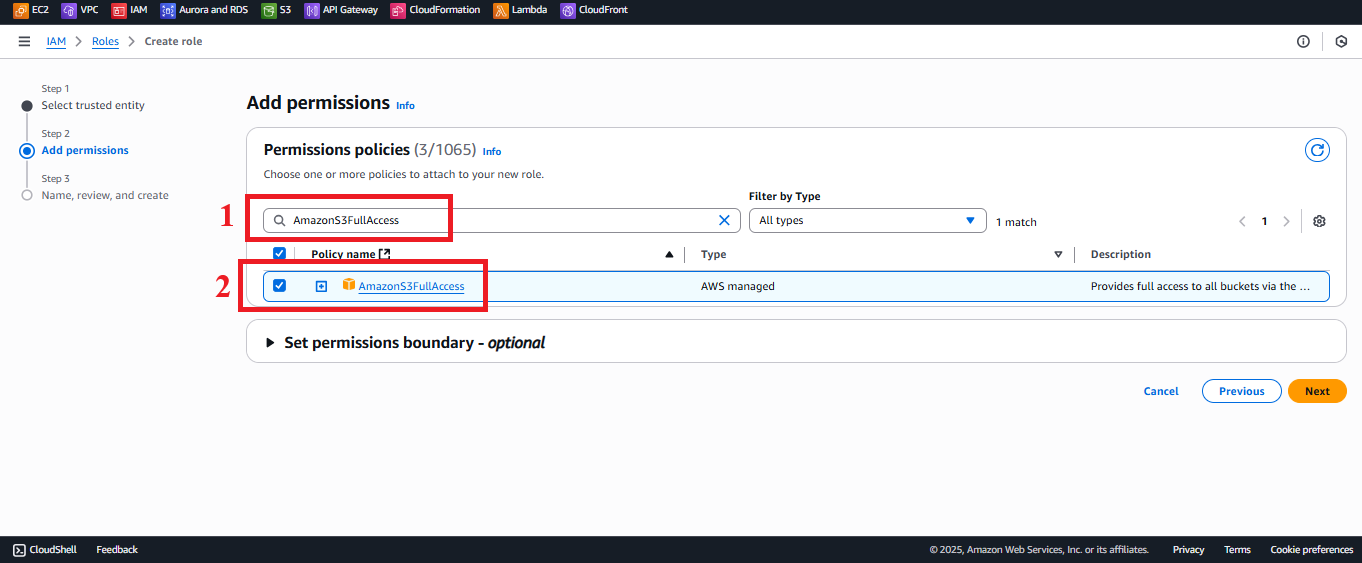 Figure 7: Selecting the AmazonS3FullAccess policy.
Figure 7: Selecting the AmazonS3FullAccess policy. - Type
-
CloudFrontFullAccess:
- Type
CloudFrontFullAccessin the search bar. - Select the CloudFrontFullAccess policy.
Description: Grants permission to manage CloudFront distributions for potential future features.
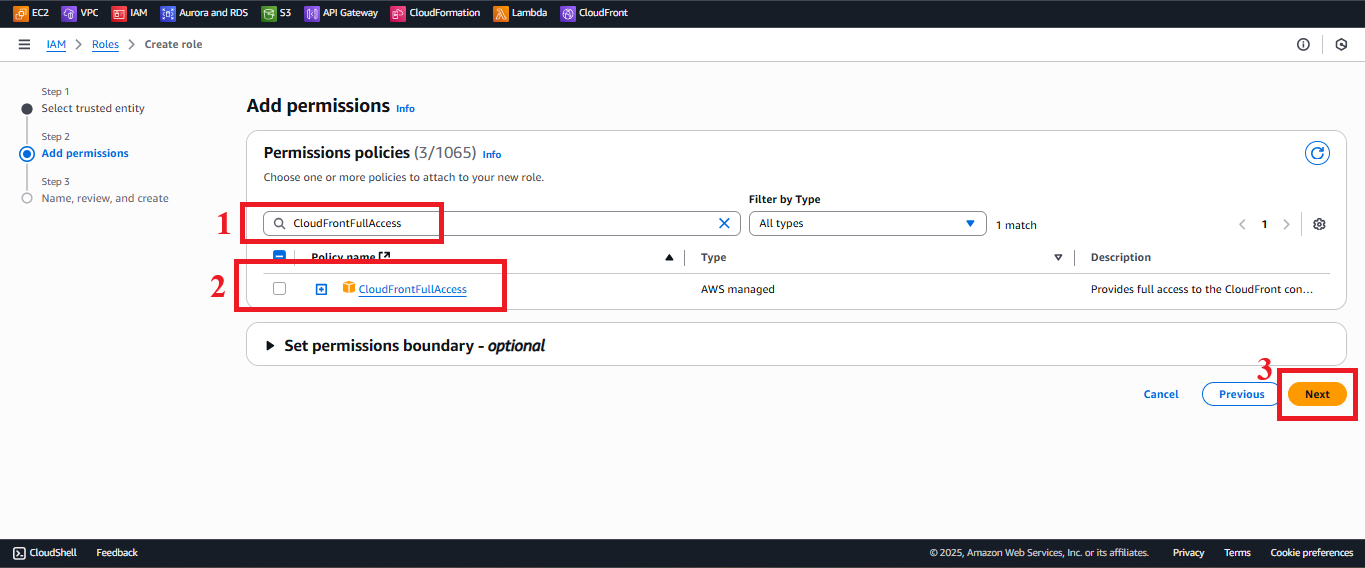 Figure 8: Selecting the CloudFrontFullAccess policy.
Figure 8: Selecting the CloudFrontFullAccess policy. - Type
-
-
Verify the list of Permissions policies to ensure it includes:
AWSLambdaBasicExecutionRoleAmazonDynamoDBReadOnlyAccessAmazonS3FullAccessCloudFrontFullAccess
-
Click Next.
6. Name and Review the Role
-
In the Role details section:
- Role Name: Enter
LambdaGetStudentRole.Note: The name must match exactly with the Lambda function configuration for
getStudentData. - Description (optional): Enter a description, e.g., “IAM role for Lambda function getStudentData, granting read access to DynamoDB, CloudWatch logging, and supporting S3/CloudFront.”
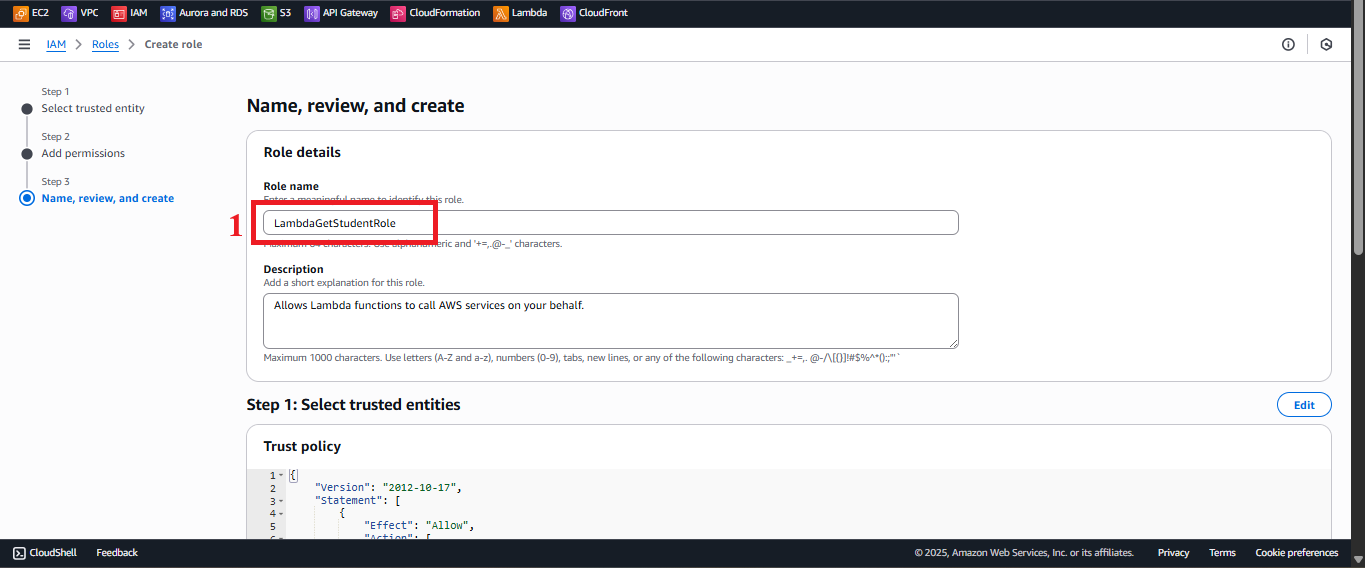 Figure 9: Enter role name and description.
Figure 9: Enter role name and description. - Role Name: Enter
-
Double-check:
- Trusted entity: AWS Service (Lambda).
- Permissions:
AWSLambdaBasicExecutionRole,AmazonDynamoDBReadOnlyAccess,AmazonS3FullAccess,CloudFrontFullAccess.
-
Click Create Role.
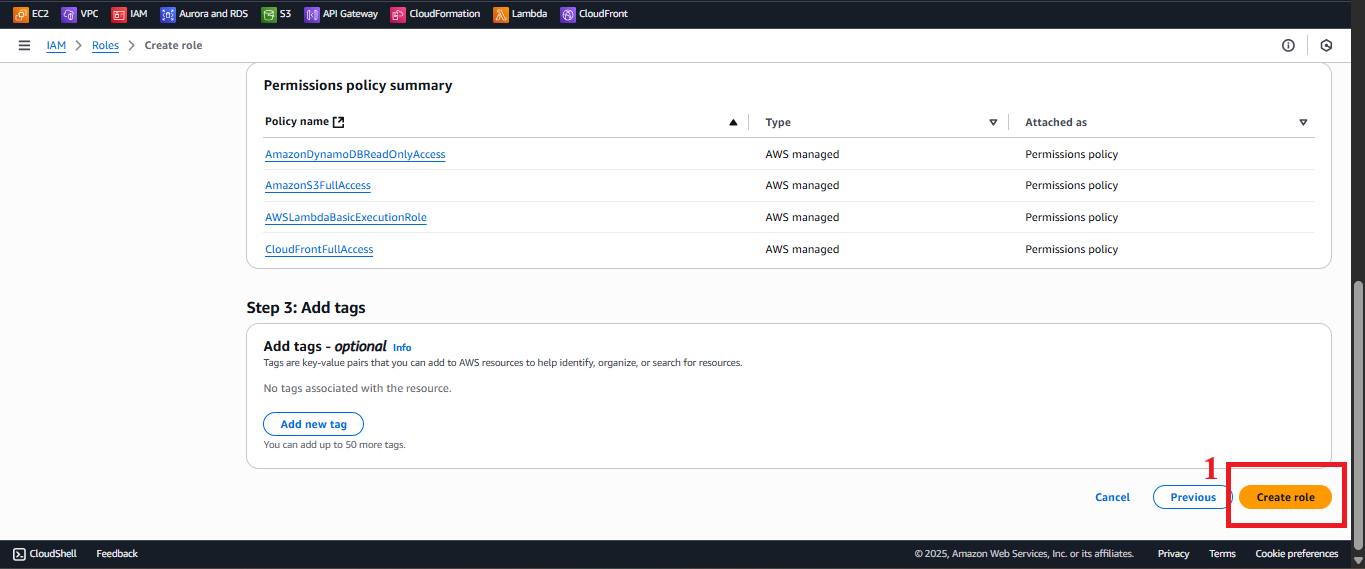 Figure 10: Create Role button to confirm.
Figure 10: Create Role button to confirm.
7. Check Role Creation Status
-
After clicking Create Role, you will return to the Roles list.
-
Find the LambdaGetStudentRole role. If successful, you should see the message: “Role LambdaGetStudentRole created”.
-
Click on LambdaGetStudentRole to view details:
- ARN: Record the ARN (e.g.,
arn:aws:iam::your-account-id:role/LambdaGetStudentRole) to use when configuring the Lambda function. - Policies: Verify the inclusion of
AWSLambdaBasicExecutionRole,AmazonDynamoDBReadOnlyAccess,AmazonS3FullAccess,CloudFrontFullAccess.
- ARN: Record the ARN (e.g.,
-
If the role does not appear, refresh the page or double-check the steps.
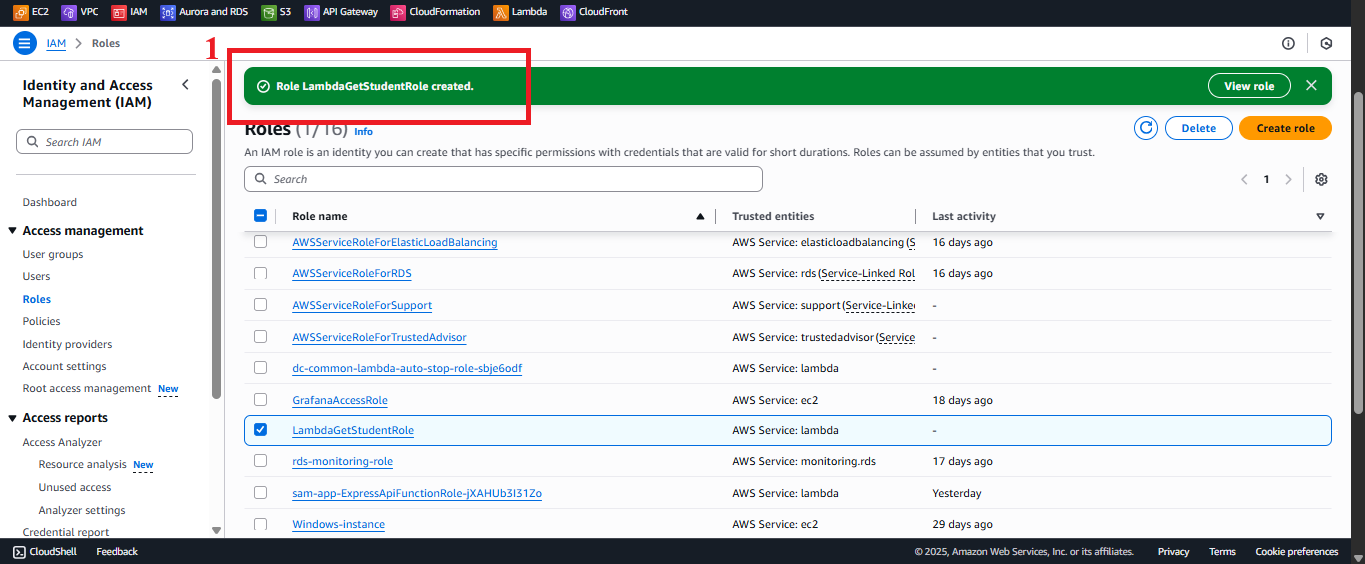 Figure 11: Role details for LambdaGetStudentRole with ARN and policies.
Figure 11: Role details for LambdaGetStudentRole with ARN and policies.
Important Notes
| Factor | Details |
|---|---|
| Role Name | Must be LambdaGetStudentRole (case-sensitive) to match the Lambda function. Incorrect names will cause execution errors. |
| S3 and CloudFront | AmazonS3FullAccess and CloudFrontFullAccess are not currently used, but kept for future functionality (e.g., storing files in S3 or managing CloudFront). Delete if unnecessary to comply with least privilege. |
| Security Optimization | Consider creating a custom policy instead of AmazonDynamoDBReadOnlyAccess to restrict access specifically to the studentData table. |
| Check Early | Record the ARN and verify the role in IAM before configuring the Lambda function to ensure proper setup. |
| Error Handling | If you encounter an “Access Denied” error, check AWS account permissions (iam:CreateRole) or contact your administrator. |
Practical Tip: Always verify the ARN and policies immediately after creating the role to confirm configuration before integrating with Lambda.
Conclusion
The IAM role LambdaGetStudentRole ensures that the Lambda function getStudentData has permissions to read data from DynamoDB, log data to CloudWatch, and support potential extensions with S3 and CloudFront. This role is now ready to be integrated into the Lambda function in the next steps.
Next Step: Proceed to Create IAM Role for Lambda Post to set up the role for the function that stores student data!